security
Why DeFi Due Diligence?
While interacting with DeFi protocols, users' and investors' funds are likely to be stolen. Due Diligence in a DeFi project is one of the crucial steps in analysing DeFi protocols before using them.
There is a steep rise in DeFi-related scams and cryptocurrencies being stolen; having a thorough analysis of the DeFi project can help avert them. Investigating a DeFi project by considering the movement of funds between address to address can save users and investors from fraudulent activities in the DeFi ecosystem that is vulnerable and should be approached cautiously.
security
Risks associated with the DeFi Ecosystem
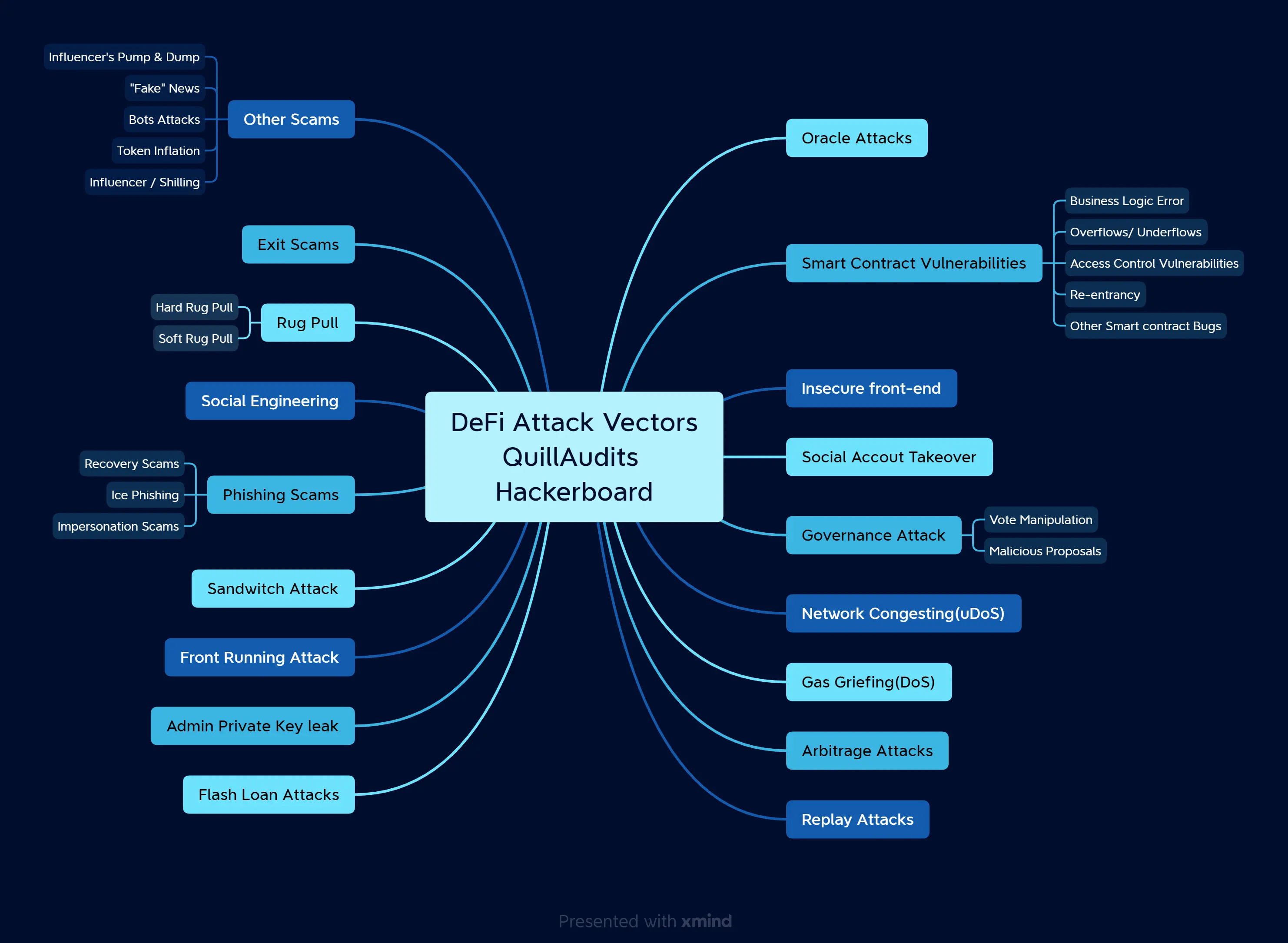
QuillAudits acknowledges the significant threats linked to the DeFi ecosystem, which can lead to many critical possibilities.
We identify ways the system is susceptible to be gamed or abused, what parts are exposed to centralisation risks like the point of interaction with oracles, and what governance mechanisms are in place that could be a potential threat to the investor funds.
Coding Risk
The complex nature of DeFi protocols is not surprising that there are errors in the code that can provide malicious parties with an attack vector through which hackers can steal funds. One such attack was on DeFi protocol SushiSwap which was exploited for between $10,000 and $15,000.
The risk posed as it is trivial for a malicious party to take control of the singular source of data and manipulate the market to their profit. Oracles are a possible source of systemic risk, and their data feeding role is prone to manipulation.
Centralization Risk
Financial Risk
DeFi protocols are based on public blockchains. These blockchains typically have a native digital asset. The price-performance of the asset of the supporting blockchain is likely to affect the value of the holdings locked in a DeFi protocol. While this may lead to profit, it is also possible that there are losses.
Unfortunately, due to a combination of factors, such as a lack of understanding and the complexities in technology, some regulators and jurisdictions are not in favour of the DeFi space. Fortunately, this issue is likely to be alleviated with time.
Regulatory Risk